ziomario
Well-Known Member
- Joined
- Jun 1, 2020
- Messages
- 4
- Thread Author
- #1
Hello.
I'm trying to prepare my system to run succesfully the SurveyDDA.ps1 script because I want to pass some device from Windows server host os to the guest OS. My motherboard is Gigabyte Aorus pro. Some time ago I've asked to Gigabyte how to enable the ACS and they sent to me the lastest BIOS upgrade. So,I went on the BIOS to check if the ACS was enabled but it was already enabled. So,good,I've installed Windows server 2019 standard edition and I've installed and enabled hyper-V. After that,I went on this website :
MicrosoftDocs/Virtualization-Documentation
and I've got the script. So.
Test done with :
ACS enabled ;
Windows server 2019 standard edition ;
Hyper-V installed and enabled ;
BIOS version : Z390AORUSPROGA9.F12g
Product Name: Z390 AORUS PRO (1.0) BIOS Ver: Z390AORUSPROGA9.F12g
Purchase Dealer: Amazon
Brand: Nvidia Model: RTX 2080 ti
Model: I9-9900k
Operating System: other - Windows server 2019 SP: 17763.rs5_release.180914-1434
HyperX-Predator Size: 32 GB
Power Supply: 600 Memory Part No.: DDR4-HX430C15PB3K2-32
PS C:\users\administrator\Desktop> .\survey-dda.ps1
Generating a list of PCI Express endpoint devices
Intel(R) USB 3.1 eXtensible Host Controller - 1.10 (Microsoft)BIOS requires that this device remain attached to BIOS-owned memory. Not assignable.
High Definition Audio ControllerOld-style PCI device, switch port, etc. Not assignable.
NVIDIA USB Type-C Port Policy ControllerBIOS kept control of PCI Express for this device. Not assignable.
Intel(R) Host Bridge/DRAM Registers - 3E30BIOS requires that this device remain attached to BIOS-owned memory. Not assignable.
NVIDIA GeForce RTX 2080 TiBIOS kept control of PCI Express for this device. Not assignable.
Intel(R) 300 Series Chipset Family SATA AHCI ControllerOld-style PCI device, switch port, etc. Not assignable.
NVIDIA USB 3.10 eXtensible Host Controller - 1.10 (Microsoft)BIOS kept control of PCI Express for this device. Not assignable.
Intel(R) Management Engine InterfaceOld-style PCI device, switch port, etc. Not assignable.
Intel(R) SMBus - A323Old-style PCI device, switch port, etc. Not assignable.
Intel(R) Thermal Subsystem - A379Old-style PCI device, switch port, etc. Not assignable.
High Definition Audio ControllerBIOS kept control of PCI Express for this device. Not assignable.
Intel(R) PCI Express Root Port #9 - A330Old-style PCI device, switch port, etc. Not assignable.
Intel(R) PCI Express Root Port #1 - A338Old-style PCI device, switch port, etc. Not assignable.
PCI standard RAM ControllerOld-style PCI device, switch port, etc. Not assignable.
Intel(R) SPI (flash) Controller - A324Old-style PCI device, switch port, etc. Not assignable.
Intel(R) PCIe Controller (x16) - 1901Old-style PCI device, switch port, etc. Not assignable.
Intel(R) UHD Graphics 630BIOS requires that this device remain attached to BIOS-owned memory. Not assignable.
Intel(R) Ethernet Connection (7) I219-VOld-style PCI device, switch port, etc. Not assignable.
Intel(R) 300 Series Chipset Family LPC Controller (Z390) - A305Old-style PCI device, switch port, etc. Not assignable.
Intel(R) PCI Express Root Port #17 - A340Old-style PCI device, switch port, etc. Not assignable.
Unfortunately, this machine doesn't support using them in a VM.
To use SR-IOV on this system, the system BIOS must be updated to allow Windows to control PCI Express. Contact your system manufacturer for an update.SR-IOV cannot be used on this system as the PCI Express hardware does not support Access Control Services (ACS) at any root port. Contact your system vendor for further information.
Infact when I tried to dismount the graphic card from Windows Server 2019,this is what happened :
PS C:\Users\Administrator\Downloads\cmder> $vmName = 'VM'
PS C:\Users\Administrator\Downloads\cmder> $instanceId = 'VEN_10DE&DEV_1E04'
PS C:\Users\Administrator\Downloads\cmder> $vm = Get-VM -Name $vmName
PS C:\Users\Administrator\Downloads\cmder> $dev = (Get-PnpDevice -PresentOnly).Where{ $_.InstanceId -like $instanceId }
PS C:\Users\Administrator\Downloads\cmder> Disable-PnpDevice -InstanceId $dev.InstanceId -Confirm:$false
OK.
PS C:\Users\Administrator\Downloads\cmder> Dismount-VMHostAssignableDevice -LocationPath "PCIROOT(0)#PCI(0100)#PCI(0000)"
Dismount-VMHostAssignableDevice : The operation failed.The current configuration does not allow for OS control of the PCI Express bus. Please check your BIOS or UEFI settings.
But,as u can see below,the ACS is enabled :
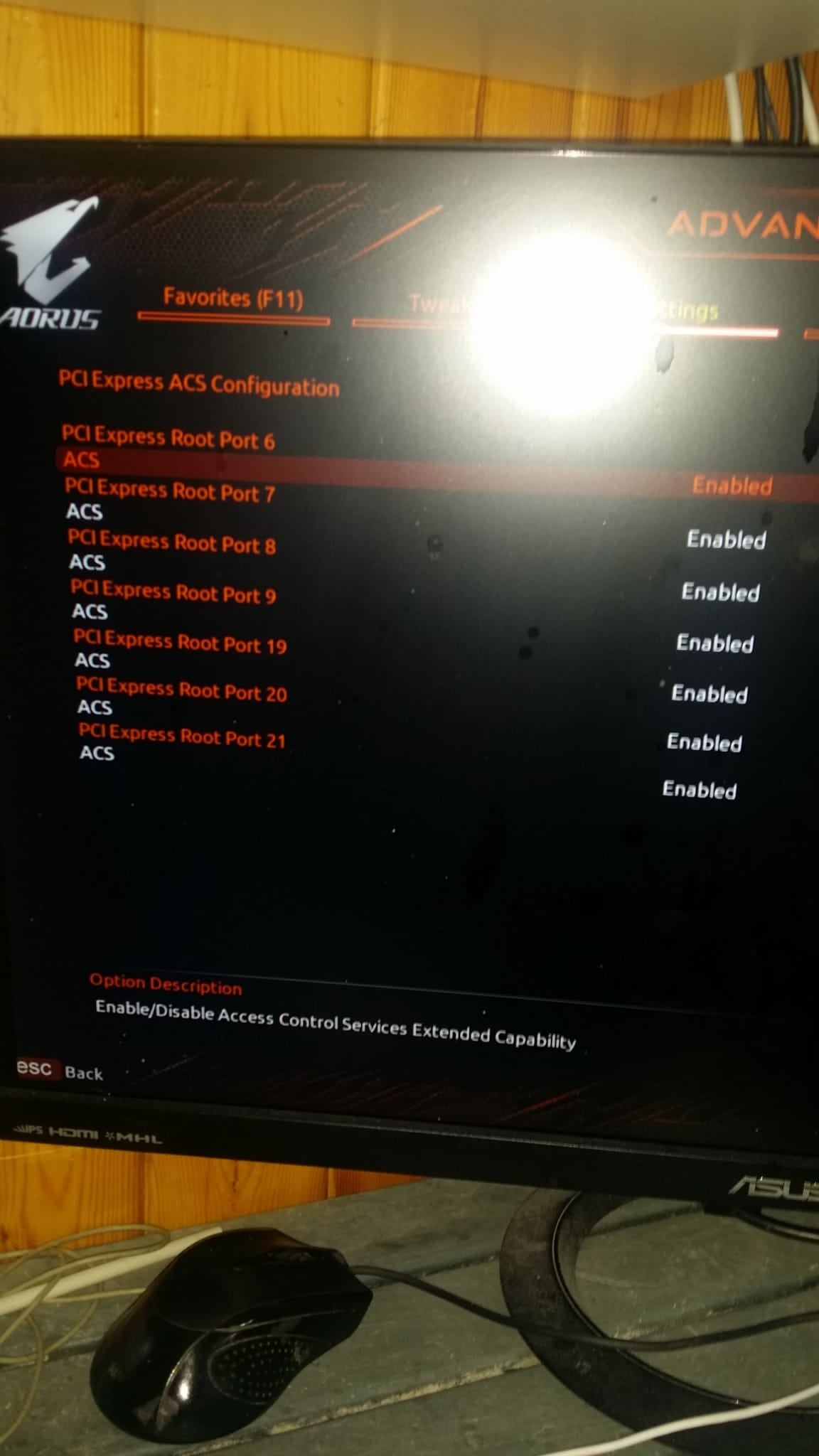
as well as the ASPM :
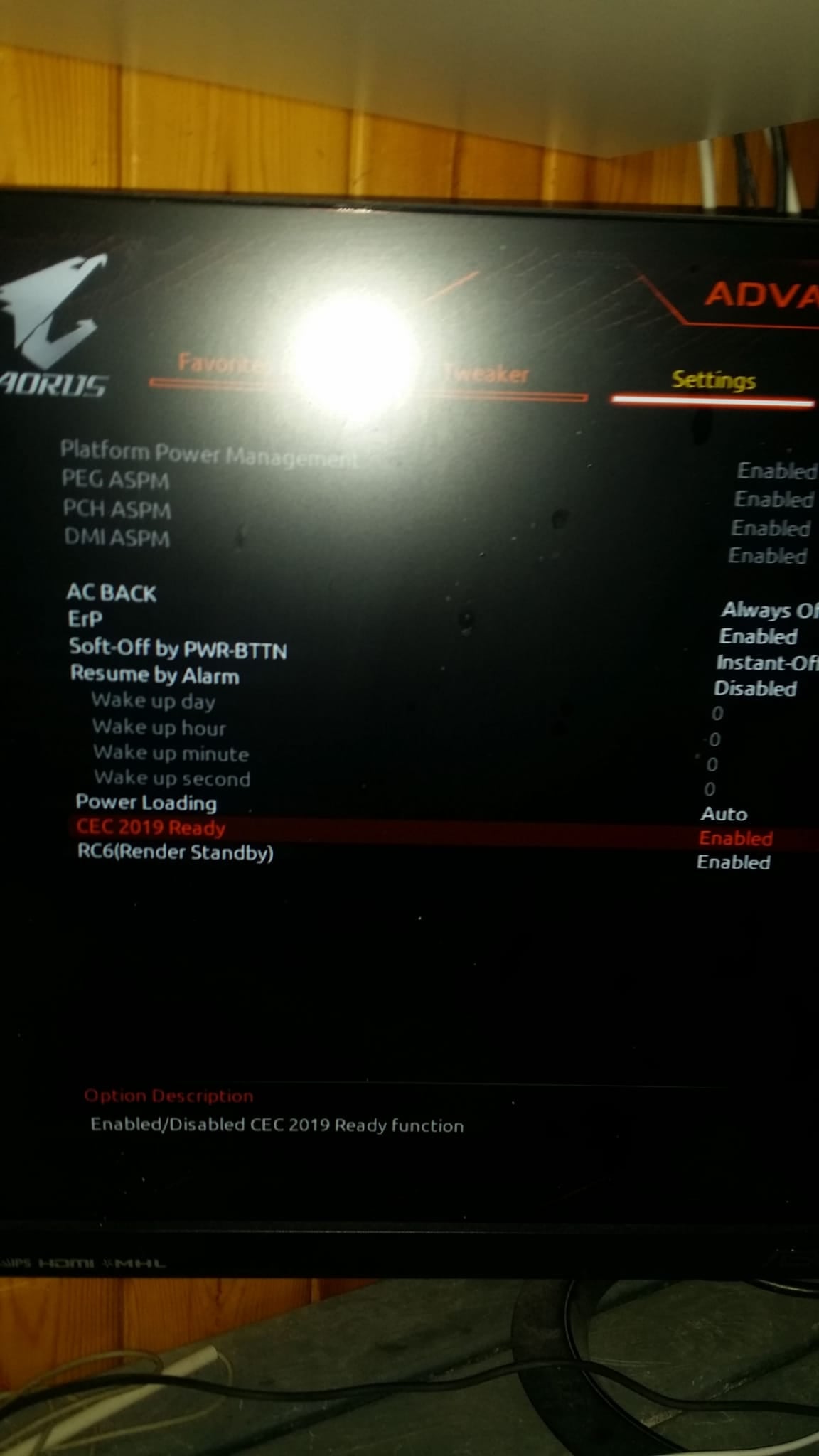
what's wrong ? what's missing ? Should I enable SR-IOV ? I don't have this option on the BIOS. Am I forgetting something ?
I'm trying to prepare my system to run succesfully the SurveyDDA.ps1 script because I want to pass some device from Windows server host os to the guest OS. My motherboard is Gigabyte Aorus pro. Some time ago I've asked to Gigabyte how to enable the ACS and they sent to me the lastest BIOS upgrade. So,I went on the BIOS to check if the ACS was enabled but it was already enabled. So,good,I've installed Windows server 2019 standard edition and I've installed and enabled hyper-V. After that,I went on this website :
MicrosoftDocs/Virtualization-Documentation
and I've got the script. So.
Test done with :
ACS enabled ;
Windows server 2019 standard edition ;
Hyper-V installed and enabled ;
BIOS version : Z390AORUSPROGA9.F12g
Product Name: Z390 AORUS PRO (1.0) BIOS Ver: Z390AORUSPROGA9.F12g
Purchase Dealer: Amazon
Brand: Nvidia Model: RTX 2080 ti
Model: I9-9900k
Operating System: other - Windows server 2019 SP: 17763.rs5_release.180914-1434
HyperX-Predator Size: 32 GB
Power Supply: 600 Memory Part No.: DDR4-HX430C15PB3K2-32
PS C:\users\administrator\Desktop> .\survey-dda.ps1
Generating a list of PCI Express endpoint devices
Intel(R) USB 3.1 eXtensible Host Controller - 1.10 (Microsoft)BIOS requires that this device remain attached to BIOS-owned memory. Not assignable.
High Definition Audio ControllerOld-style PCI device, switch port, etc. Not assignable.
NVIDIA USB Type-C Port Policy ControllerBIOS kept control of PCI Express for this device. Not assignable.
Intel(R) Host Bridge/DRAM Registers - 3E30BIOS requires that this device remain attached to BIOS-owned memory. Not assignable.
NVIDIA GeForce RTX 2080 TiBIOS kept control of PCI Express for this device. Not assignable.
Intel(R) 300 Series Chipset Family SATA AHCI ControllerOld-style PCI device, switch port, etc. Not assignable.
NVIDIA USB 3.10 eXtensible Host Controller - 1.10 (Microsoft)BIOS kept control of PCI Express for this device. Not assignable.
Intel(R) Management Engine InterfaceOld-style PCI device, switch port, etc. Not assignable.
Intel(R) SMBus - A323Old-style PCI device, switch port, etc. Not assignable.
Intel(R) Thermal Subsystem - A379Old-style PCI device, switch port, etc. Not assignable.
High Definition Audio ControllerBIOS kept control of PCI Express for this device. Not assignable.
Intel(R) PCI Express Root Port #9 - A330Old-style PCI device, switch port, etc. Not assignable.
Intel(R) PCI Express Root Port #1 - A338Old-style PCI device, switch port, etc. Not assignable.
PCI standard RAM ControllerOld-style PCI device, switch port, etc. Not assignable.
Intel(R) SPI (flash) Controller - A324Old-style PCI device, switch port, etc. Not assignable.
Intel(R) PCIe Controller (x16) - 1901Old-style PCI device, switch port, etc. Not assignable.
Intel(R) UHD Graphics 630BIOS requires that this device remain attached to BIOS-owned memory. Not assignable.
Intel(R) Ethernet Connection (7) I219-VOld-style PCI device, switch port, etc. Not assignable.
Intel(R) 300 Series Chipset Family LPC Controller (Z390) - A305Old-style PCI device, switch port, etc. Not assignable.
Intel(R) PCI Express Root Port #17 - A340Old-style PCI device, switch port, etc. Not assignable.
Unfortunately, this machine doesn't support using them in a VM.
To use SR-IOV on this system, the system BIOS must be updated to allow Windows to control PCI Express. Contact your system manufacturer for an update.SR-IOV cannot be used on this system as the PCI Express hardware does not support Access Control Services (ACS) at any root port. Contact your system vendor for further information.
Infact when I tried to dismount the graphic card from Windows Server 2019,this is what happened :
PS C:\Users\Administrator\Downloads\cmder> $vmName = 'VM'
PS C:\Users\Administrator\Downloads\cmder> $instanceId = 'VEN_10DE&DEV_1E04'
PS C:\Users\Administrator\Downloads\cmder> $vm = Get-VM -Name $vmName
PS C:\Users\Administrator\Downloads\cmder> $dev = (Get-PnpDevice -PresentOnly).Where{ $_.InstanceId -like $instanceId }
PS C:\Users\Administrator\Downloads\cmder> Disable-PnpDevice -InstanceId $dev.InstanceId -Confirm:$false
OK.
PS C:\Users\Administrator\Downloads\cmder> Dismount-VMHostAssignableDevice -LocationPath "PCIROOT(0)#PCI(0100)#PCI(0000)"
Dismount-VMHostAssignableDevice : The operation failed.The current configuration does not allow for OS control of the PCI Express bus. Please check your BIOS or UEFI settings.
But,as u can see below,the ACS is enabled :

as well as the ASPM :

what's wrong ? what's missing ? Should I enable SR-IOV ? I don't have this option on the BIOS. Am I forgetting something ?