- Thread Author
- #1
AD :Backup operators privileges added to user are getting reflected or applied.
The user is added to Backup operators Privilege member group the privileges are not being reflected in CLI .
Below are the configuration, Expected, and Actual Privileges.
Config: bo user is member of Backup Operators group.
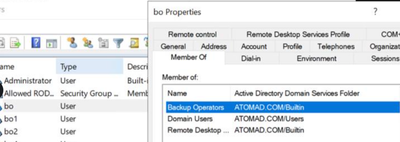
Expected Permissions:
SeBackupPrivilege
SeRestorePrivilege
SeChangeNotifyPrivilege
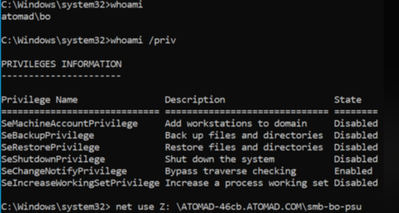
Actual Permissions:
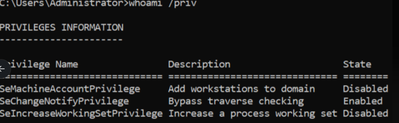
This was working fine till the 2nd -3rd week of December, but this is not working in the last few days. Tried with different windows VMs
windows image: windows-server-2022-dc-v20231115
I am trying to use the below Documents as reference for validation.Backup User
The user is added to Backup operators Privilege member group the privileges are not being reflected in CLI .
Below are the configuration, Expected, and Actual Privileges.
Config: bo user is member of Backup Operators group.
Expected Permissions:
SeBackupPrivilege
SeRestorePrivilege
SeChangeNotifyPrivilege
Actual Permissions:
This was working fine till the 2nd -3rd week of December, but this is not working in the last few days. Tried with different windows VMs
windows image: windows-server-2022-dc-v20231115
I am trying to use the below Documents as reference for validation.Backup User