A little background. Each running service has corresponding registry entries. One in particular, ImagePath contains the command executed when a service starts. It is a moderate vulnerability when the ImagePath is not quoted. What can happen is an attacker can make the service execute any arbitrator executable with whatever privileges that service has. In some cases with the SYSTEM account. Here is a command that can be run to locate unquoted image paths which you can then edit the ImagePath value and add double quotes around it.
Services are located in the registry at HKEY_LOCALMACHINE\SYSTEM\CurrentControlSet\Services each key represents a service.
Open a command prompt and run the following command
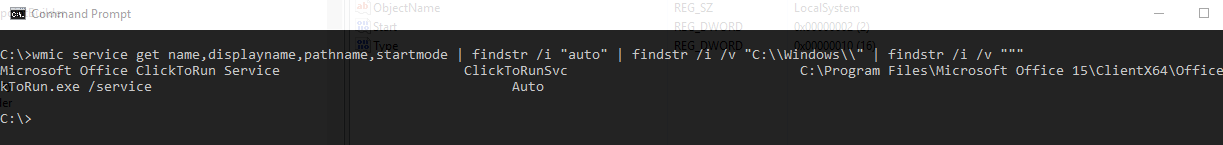
From my example we see I found one on my system. (I really just unquoted it)
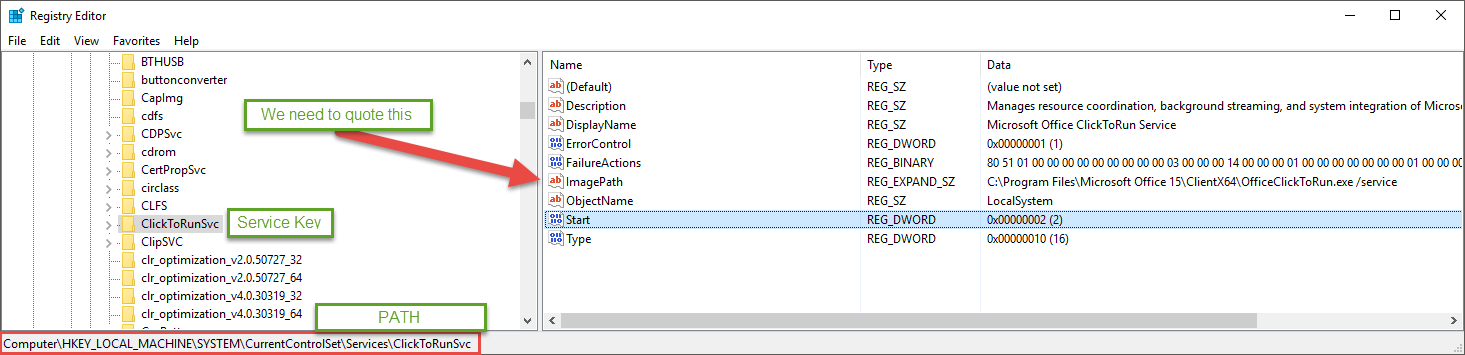
Now open regedit and navigate to the key corresponding to the service name ClickToRunSvc from the path mentioned above. You will see the the path has a space and no quotes around the exe.
Double click the ImagePath value and add double quotes ONLY AROUND THE EXE PATH don't add them around any switches
Here it is fixed

Rinse and repeat.
Congratulations, you have just patched one or more security vulnerabilities!
Services are located in the registry at HKEY_LOCALMACHINE\SYSTEM\CurrentControlSet\Services each key represents a service.
Open a command prompt and run the following command
Code:
wmic service get name,displayname,pathname,startmode | findstr /i "auto" | findstr /i /v "C:\\Windows\\" | findstr /i /v """From my example we see I found one on my system. (I really just unquoted it)
Now open regedit and navigate to the key corresponding to the service name ClickToRunSvc from the path mentioned above. You will see the the path has a space and no quotes around the exe.
Double click the ImagePath value and add double quotes ONLY AROUND THE EXE PATH don't add them around any switches
Here it is fixed
Rinse and repeat.
Congratulations, you have just patched one or more security vulnerabilities!