- Joined
- Aug 12, 2011
I'm going to post this in efforts to help prevent individuals from getting a possible Virus. I've known this for a while now, and the fact is, Digital Signatures may not all be legit. Therefore, not all are to be trusted.
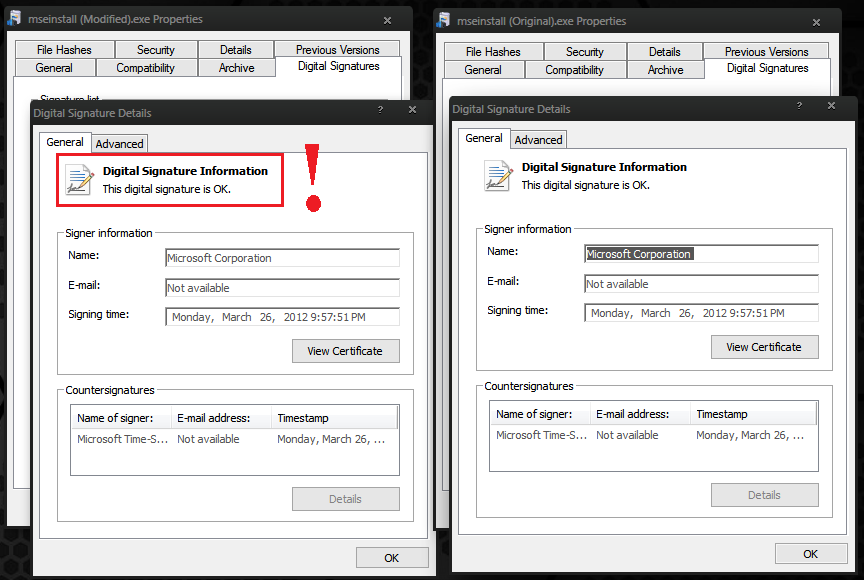
It is possible to modify a file and append junk data to EOF of a file without the signature becoming invalidated. I did a test in Windows 7 a few months ago with the installation file for Microsoft Security Essentials (mseinstall.exe). As long as the additional bytes were of a multiple of FileAlignment specified in the Optional Header (FileAlignment property for this Microsoft Security Essentials was 200 bytes in this case), you could increase the size of the certificate within the Data Directories along with a few other binary modifications to change the size of the certificate itself in the first 4 bytes, and you would not trigger the conditions for the file's certificate to invalidate. This means that the file was modified, but still shown to be signed by Microsoft, and supposedly unchanged/unmodified since the time the signature was added to the file, which we know was not true because I did in fact change the file.
This shouldn't happen... The point of Digital Signatures is so that if a file is modified in ANY way, that signature is invalidated, telling the user that it has been changed since it was last signed by the author.
After that, you'd be able to update the checksum in Optional Header as well without the file signature invalidating too, but that's only necessary if the file was a boot program really.
But until that much can be further taken advantage of, (and myself nor the Microsoft security team were able to find a problem with it yet,) this only becomes even more critical if the digest hash used with the certificate IS a broken hash algorithm like MD5.
So the moral of my story, don't trust Digital Signatures, that were signed with the MD5 hashing algorithm!!!
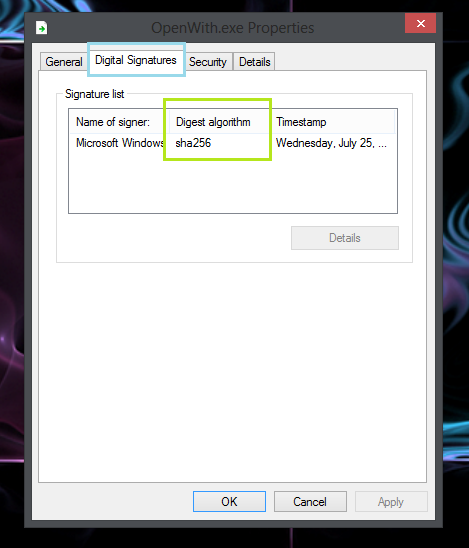
You can see what hash was used through the file properties of a file containing a digital signature:
Proof of concept, with testing I did in Windows 7:
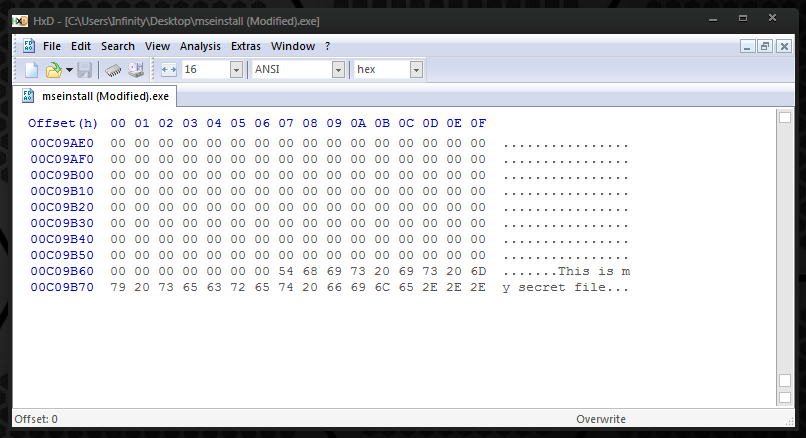
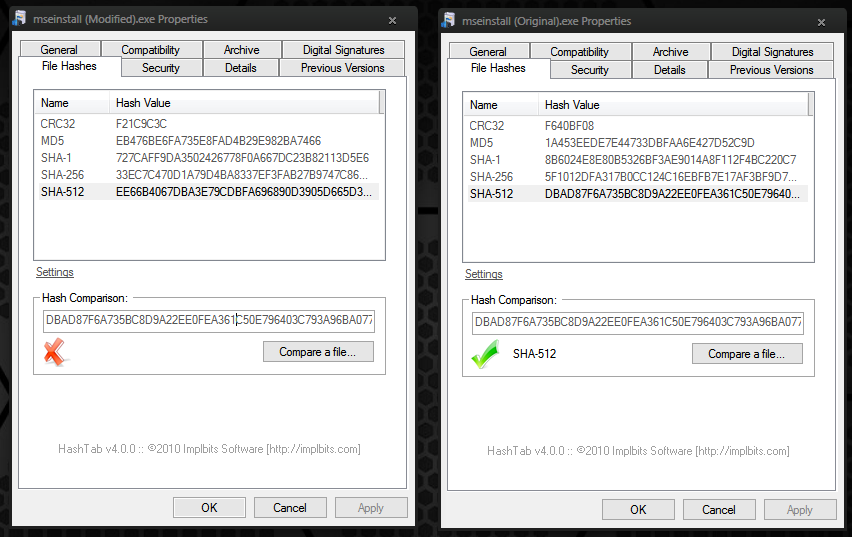
It is possible to modify a file and append junk data to EOF of a file without the signature becoming invalidated. I did a test in Windows 7 a few months ago with the installation file for Microsoft Security Essentials (mseinstall.exe). As long as the additional bytes were of a multiple of FileAlignment specified in the Optional Header (FileAlignment property for this Microsoft Security Essentials was 200 bytes in this case), you could increase the size of the certificate within the Data Directories along with a few other binary modifications to change the size of the certificate itself in the first 4 bytes, and you would not trigger the conditions for the file's certificate to invalidate. This means that the file was modified, but still shown to be signed by Microsoft, and supposedly unchanged/unmodified since the time the signature was added to the file, which we know was not true because I did in fact change the file.
This shouldn't happen... The point of Digital Signatures is so that if a file is modified in ANY way, that signature is invalidated, telling the user that it has been changed since it was last signed by the author.
After that, you'd be able to update the checksum in Optional Header as well without the file signature invalidating too, but that's only necessary if the file was a boot program really.
But until that much can be further taken advantage of, (and myself nor the Microsoft security team were able to find a problem with it yet,) this only becomes even more critical if the digest hash used with the certificate IS a broken hash algorithm like MD5.
So the moral of my story, don't trust Digital Signatures, that were signed with the MD5 hashing algorithm!!!
You can see what hash was used through the file properties of a file containing a digital signature:

Proof of concept, with testing I did in Windows 7:



Last edited by a moderator:
 ), and this allowed the bad file to appear legit with a valid signature signed by Adobe to the end user.
), and this allowed the bad file to appear legit with a valid signature signed by Adobe to the end user.