reghakr
Essential Member
- Joined
- Jan 26, 2009
- Messages
- 14,186
- Thread Author
- #1
Over 100,000 Android users may have been affected by malicious apps, as 26 more malware programs have been identified on Google’s Android Market.
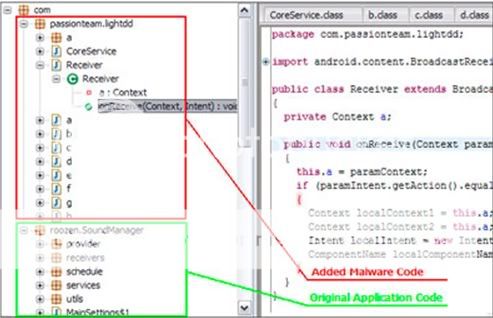
Link Removed - Invalid URL made the discovery over the weekend, and believes that the rogue software was likely created by the same persons who created the ‘DroidDream’ malware that was discovered in dozens of Android apps a couple of months back.
The security firm followed up tips from legitimate developers who had noticed that their apps were being redistributed with modified code, and subsequently discovered a new stripped-down version of the same DroidDream code, which they’ve since dubbed ‘Droid Dream Light’.
Lookout has already informed Google of its discoveries, which has resulted in the offending apps being withdrawn from the Market.
According to Lookout, once installed on a user’s device, the user doesn’t even have to open the apps for their device to be at risk; the code can be activated by an external triggering event, such as an incoming voice call, which then prompts the device to send data to a remote server, such as the IMEI number and information about installed programs.
Google may choose to activate its ‘app kill switch’ to remotely wipe the problem programs from users’ devices, but for now, check the list below to see whether or not you may have infected apps installed on your device, and visit Lookout for more information on how to deal with them.
The list of infected apps includes:
Magic Photo Studio
•Sexy Girls: Hot Japanese
•Sexy Legs
•HOT Girls 4
•Beauty Breasts
•Sex Sound
•Sex Sound: Japanese
•HOT Girls 1
•HOT Girls 2
•HOT Girls 3
Mango Studio
•Floating Image Free
•System Monitor
•Super StopWatch and Timer
•System Info Manager
E.T. Tean
•Call End Vibrate
BeeGoo
•Quick Photo Grid
•Delete Contacts
•Quick Uninstaller
•Contact Master
•Brightness Settings
•Volume Manager
•Super Photo Enhance
•Super Color Flashlight
•Paint Master
DroidPlus
•Quick Cleaner
•Super App Manager
•Quick SMS Backup
Source: Neowin.net - Android Market: thousands affected as 26 new malware apps discovered
Link Removed - Invalid URL made the discovery over the weekend, and believes that the rogue software was likely created by the same persons who created the ‘DroidDream’ malware that was discovered in dozens of Android apps a couple of months back.
The security firm followed up tips from legitimate developers who had noticed that their apps were being redistributed with modified code, and subsequently discovered a new stripped-down version of the same DroidDream code, which they’ve since dubbed ‘Droid Dream Light’.
Lookout has already informed Google of its discoveries, which has resulted in the offending apps being withdrawn from the Market.
According to Lookout, once installed on a user’s device, the user doesn’t even have to open the apps for their device to be at risk; the code can be activated by an external triggering event, such as an incoming voice call, which then prompts the device to send data to a remote server, such as the IMEI number and information about installed programs.
Google may choose to activate its ‘app kill switch’ to remotely wipe the problem programs from users’ devices, but for now, check the list below to see whether or not you may have infected apps installed on your device, and visit Lookout for more information on how to deal with them.
The list of infected apps includes:
Magic Photo Studio
•Sexy Girls: Hot Japanese
•Sexy Legs
•HOT Girls 4
•Beauty Breasts
•Sex Sound
•Sex Sound: Japanese
•HOT Girls 1
•HOT Girls 2
•HOT Girls 3
Mango Studio
•Floating Image Free
•System Monitor
•Super StopWatch and Timer
•System Info Manager
E.T. Tean
•Call End Vibrate
BeeGoo
•Quick Photo Grid
•Delete Contacts
•Quick Uninstaller
•Contact Master
•Brightness Settings
•Volume Manager
•Super Photo Enhance
•Super Color Flashlight
•Paint Master
DroidPlus
•Quick Cleaner
•Super App Manager
•Quick SMS Backup
Source: Neowin.net - Android Market: thousands affected as 26 new malware apps discovered